Acuity Brands Security Vulnerability Policy
This policy relates to the investigation and disclosure of security vulnerabilities that potentially affect products and services provided by Acuity Brands.

Acuity Brands Lighting Product Security Incident Response
The Acuity Brands Product Security Incident Response Team (PSIRT) is responsible for coordinating stakeholder interests regarding security concerns that potentially affect Acuity Brands products and services. In this pursuit, the PSIRT manages the receipt, investigation, and notification procedure regarding security vulnerabilities and other issues affecting our cloud-based infrastructure. The Acuity Brands PSIRT works with customers, consultants, security researchers, academic institutions, and other vendors to handle potential security issues discovered within Acuity Brands products and services.

Reporting a Security Vulnerability
Individuals or organizations that are aware of a product security issue are strongly encouraged to contact the PSIRT. Timely identification of security vulnerabilities is critical to eliminating potential threats. Acuity Brands welcomes reports from independent researchers, industry organizations, vendors, customers, and other sources concerned with product or network security and is committed to responsible disclosure.
If you believe you have identified a potential security vulnerability, you may contact the Acuity Brands PSIRT through our email alias, psirt@acuitybrands.com. The PSIRT will identify the appropriate product teams in order to address the issue.
Acuity encourages the encryption of sensitive information that is sent to the PSIRT. The Acuity Brands PSIRT supports encrypted messages via PGP/GNU Privacy Guard. The Acuity Brands PSIRT public PGP key psirt@acuitybrands.com (204DDE2C) is available on multiple public key servers.
When reporting potential security issues, please include as much of the below information as possible to help the PSIRT understand the nature and scope of the potential vulnerability:
- Product name and version that contains the vulnerability
- Step-by-step instructions to reproduce the vulnerability
- Proof-of-concept or exploit code
- Potential impact of the vulnerability, including how an attacker could exploit the vulnerability
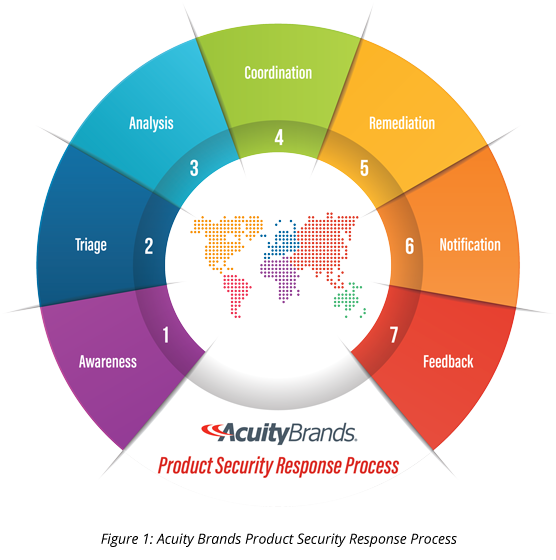
Acuity Brands Product Security Incident Response Process
The Acuity Brands PSIRT process was developed using the ISO 30111 standard and documentation from the Forum of Incident Response and Security Teams (FIRST) as guides. The following figure provides a high-level view of our response process.
The following are the steps in the process illustrated in Figure 1. After each step is completed, the Acuity Brands PSIRT determines the appropriate actions; therefore, some of these steps might not be performed for some issues.
- Awareness: information is received regarding a potential security vulnerability
- Triage: the report is validated, prioritized, and resources identified
- Analysis: impact assessment is conducted and remediation plan developed
- Coordination: all collaborators are made aware of the timelines
- Remediation: fixes are released and cloud-based services are updated
- Notification: affected customers are notified
- Feedback: post-remediation activities are performed
Once an issue is reported to the Acuity Brands PSIRT, it is evaluated based on the potential impact of the vulnerability. The PSIRT will work with the reporter and product development teams in order to determine the severity and scope of the reported issue.
In general, the PSIRT uses the Common Vulnerability Scoring System version 3.1 (CVSS v3.1) to determine the severity level of identified vulnerabilities. If there is a security issue with a third-party software component used in an Acuity Brands product, the CVSS may be adjusted to reflect the impact to our products. CVSS is maintained by FIRST and more information may be obtained from the FIRST.org website.
After the severity and scope of the issue have been determined, the PSIRT works with appropriate internal and external resources, as needed, in order to determine the availability of fixes and a communication plan. During the investigation, Acuity Brands treats all non-public information as highly confidential. We maintain all records regarding the identified vulnerability on encrypted filesystems and distribution is limited to those individuals who can actively assist in the resolution or have a legitimate need to know. Similarly, the Acuity Brands PSIRT asks those reporting a vulnerability to maintain strict confidentiality until the details have been published through the appropriate coordinated disclosure. See the next section of this policy for information regarding disclosure criteria.
After publication of any security issue, the PSIRT reviews our secure development lifecycle and continues to monitor networks for signs of active exploitation.
Receiving Security Vulnerability Information from Acuity Brands
Acuity Brands may communicate security information privately to affected customers and publicly through Product Security Bulletins. Not all security issues will have both private and public disclosure components. Public Product Security Bulletins are published on the Acuity Brands PSIRT site (www.acuitybrands.com/psirt) when any of the following occur:
- Acuity Brands is not able to identify affected customers
- Software updates are available for all affected products
- There is public concern about the issue
- There is public discussion about a vulnerability
- There will be no fix created for affected products
Individuals may also subscribe to Acuity Brands Public Security Bulletins through email directly from the PSIRT page.
Security Bulletins summarize a vulnerability or other security issue to help customers evaluate risks present in their environments. They are not intended to help readers reproduce the issue for testing or other research. In general, Security Bulletins will include:
- Products and versions affected
- The severity rating for the vulnerability
- Brief description of the vulnerability and potential impact if exploited
- Remedy details with update/workaround information
Acuity Brands provides Security Bulletins to bring potentially important security information to the attention of stakeholders. However, Security Bulletins are provided “as-is” with no express or implied warranty and Acuity Brands does not represent that Security Bulletins are complete or accurate. Readers are responsible for confirming the accuracy of the information set forth in Security Bulletins, determining the applicability of the information to their installation, and taking whatever resulting action they may deem necessary, if any.
Brands Covered by this Policy
This policy covers all software and firmware sold by Acuity Brands. This includes, but is not limited to, the products sold under the following brands: Atrius™, DGLogik™, Dark To Light® (DTL), Distech Controls®, EldoLED®, Fresco™, Holophane®, IOTA®, nLight®, nLight® AIR, ROAM®, SensorSwitch™, Synergy®, and XPoint Wireless®.




